Overview
Preventing access for unknown users and bad actors is essential in protecting your organization from data breaches and other fraudulent activities that may lead to lost revenue, damaged brand reputation, and significant mitigation costs.
ForgeRock Identity Cloud offers several capabilities for preventing access for unknown users and bad actors, whilst allowing legitimate users seamless and secure access. These include:
- Threat detection
- AI behavioral context and User Entity Behavior Analytics (UEBA)
- Mult-factor authentication (MFA)
- Account Takeover (ATO) prevention
NOTE: To gain insights into data breaches across various industries and regions, see the 2023 ForgeRock Identity Breach Report.
Threat detection
What is it?
With threat detection, you can detect cyber attacks through multiple types of attack vectors, such as credential stuffing, brute force attacks, bot attacks, impossible travelers, known malicious IPs, and anomalous user behavior
How is it achieved in Identity Cloud?
Identity Cloud offers an Autonomous Access service that uses an Artificial Intelligent (AI) and machine learning (ML) analytics engine for real-time detection of the following threat types:
- Anomaly detection
- Double jeopardy
- Credential stuffing
- Suspicious IP
- Automated user agent filter
- Impossible travelers
- Brute force attacks
- Distributed attacks
- Suspicious IP addresses
For further information on each of these threat types, see Autonomous Access real time threat detection.
Through its AI/ML engine, Autonomous Access can assign a level of risk to the likelihood that any or all of the threat types will occur. This risk level can impact the end user’s login flow. For example, in situations of very high risk, the authentication can be stopped altogether, whereas medium-risk situations may prompt for more authentication factors.
Using Autonomous Access in conjunction with ForgeRock’s Intelligent Access Journeys, you can create login journeys that detect the threat level and adjust the end user’s login journey accordingly depending on a risk score.

Example authentication journey with Autonomous Access nodes
The Autonomous Access Signal node sets the heuristics and/or anomaly detection to be included in risk score generation. You can select or deselect the required threat types:
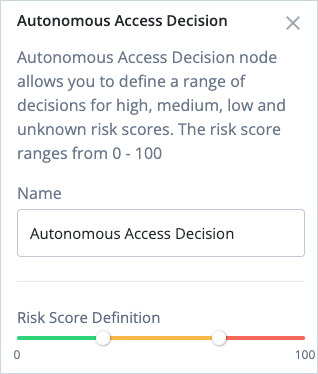
The Autonomous Access Decision node allows you to adjust the risk score definition for risk high, medium, low, and unknown scores:
For further information on achieving threat detection with Identity Cloud, see:
- ForgeRock Autonomous Access
- Autonomous Access
- Autonomous Access White Paper
- Use case: Configure risk-based authentication in ForgeRock Identity Cloud
- Use case: Configure which authentication methods are invoked based on a risk score in ForgeRock Identity Cloud
Business benefits
Identifying and responding to potential security threats in real time allows organizations to reduce the likelihood of costly security incidents associated with unauthorized access attempts, data breaches, and insider threats.
Threat detection also helps in the swift containment and remediation of cyber attacks and security breaches, reducing the time it takes to recover from an incident and minimizing the associated financial losses.
Further, compliance with industry regulations and data protection laws becomes easier when you can demonstrate robust security measures, potentially avoiding hefty fines and reputational damage.
AI behavioral context and User Entity Behavior Analytics (UEBA)
With AI behavioral context and UEBA, you can gather insight into normal user activity and then detect anomalies in behavior that indicate the potential for malicious activity. Many user behavior analytics systems utilize AI and ML to constantly adapt to keep up with the changing threat landscape.
While traditional access management systems rely on predefined rules and policies, UEBA takes a more proactive approach, using machine learning and behavioral analysis to identify anomalies and potential security incidents that might otherwise go unnoticed.
How is it achieved in Identity Cloud?
Identity Cloud offers an Autonomous Access service that provides an AI/ML engine that can learn user behavior over time. It can base a user’s behavior on the entire population, a group of users or an individual user.
By using Autonomous Access in conjunction with ForgeRock’s Intelligent Access Journeys, the authentication journey can be adjusted based on the risk associated with the user behavior at the time of authentication.
The Anomaly Detection signal in the Autonomous Access Signal node can effectively identify online anomalies in a user’s behavioral profile. It utilizes machine learning to analyze network activity and detect any deviations from a user’s typical online behavior.
Autonomous Access also has the ability to learn how the risk event was concluded so that it can learn if it was the real user or an actual attack attempt. It continuously gets smarter at identifying the difference between normal behaviors and emerging threat patterns
For further information on achieving AI behavioral context and UEBA with Identity Cloud, see:
- ForgeRock Autonomous Access
- Autonomous Access
- Autonomous Access White Paper
- Use case: Configure risk-based authentication in ForgeRock Identity Cloud
- Use case: Configure which authentication methods are invoked based on a risk score in ForgeRock Identity Cloud
Business benefits
AI behavioral context and UEBA help improve an organization’s security posture by continuously monitoring user activities. By detecting abnormal behavior, such as unauthorized access attempts or suspicious login patterns, security teams can be alerted to potential threats in real-time.
For workforce use cases, UEBA can detect abnormal behavior from employees or partners who may be engaging in unauthorized or harmful activities. UEBA enhances compliance efforts by providing better visibility into user activities and access controls, making audits and reporting more robust. This can contribute to data loss prevention efforts, helping organizations safeguard sensitive information and intellectual property.
Multi-factor authentication
What is it?
With multi-factor authentication (MFA), identities are verified through two or more categories of authentication. A common definition of authentication categories is something you know (such as a password), something you have (such as a one-time passcode), and something you are (such as a biometric). This provides a more secure method for users to access their accounts.
Multi-Factor Authentication provides more assurance that the person logging on is who they claim to be.
Since data breaches and fraud have escalated in recent years, the need for multi-factor authentication has become critical to reducing risk. In authentication flows, MFA may be requested for every authentication or only when there is an elevated risk.
How is it achieved in Identity Cloud?
To achieve MFA in Identity Cloud you can simply configure Intelligent Access Journeys with at least one authentication node from two or more authentication categories.
ForgeRock ships with a range of MFA options including:
- Open Authentication (OATH) to enable one-time password (OTP) authentication.
- Push authentication to receive push notifications on a device as part of the authentication process.
- Web Authentication (WebAuthn) to authenticate by using an authenticator device such as a fingerprint scanner on a laptop or phone.
For example, this user journey shows how you can construct a simple one-time password authentication flow using OATH nodes:
The journey can be easily extended to include out-of-the-box nodes to enable the user to obtain an authenticator app, register an MFA device or skip the registration process, or opt out of MFA.
For more advanced authentication capabilities, you can extend journeys with ForgeRock Marketplace nodes by integrating third-party services into your user journeys. These may include nodes for identity proofing, fraud protection, behavioral biometrics, and more.
For further information on achieving MFA with Identity Cloud, see:
- Multi-factor authentication
- Does the ForgeRock solution offer multi-factor authentication (MFA)?
- Use case: Configure OATH-based token two-factor authentication in ForgeRock Identity Cloud
- Use case: View the riskiest users and locations based on past activity in ForgeRock Identity Cloud
- Multi-Factor Authentication (training video)
- Stop Breaches, Not Users
- Experience dynamic MFA (ForgeRock Experience Center demo)
Business benefits
By adding an extra layer of security to protect applications and services, MFA significantly reduces the risk of unauthorized access, phishing attacks and password breaches. Additional factors, such as one-time passcodes and biometric checks, make it significantly more difficult for attackers to impersonate legitimate users.
Many industries and regions have specific data protection regulations that require the implementation of strong authentication mechanisms. For example, the Payment Card Industry Data Security Standard (PCI DSS), General Data Protection Regulation (GDPR), or Health Insurance Portability and Accountability Act (HIPAA). MFA helps organizations comply with these requirements.
If an organization handles customer data, implementing MFA can also enhance trust by demonstrating a commitment to protecting sensitive information, fostering customer loyalty, and improving the organization’s reputation.
Account Takeover (ATO) prevention
Account Takeover (ATO) fraud occurs when a malicious outsider gains access to a user’s login credentials. Typically, the perpetrators digitally break into an account through a variety of techniques, such as phishing, malware, and man-in-the-middle attacks. Once they gain access, the attackers may steal money from an account by making fraudulent transactions, such as payment to a fake company, transferring funds to another bank account, or through any number of unauthorized transactions.
With ATO prevention, you can apply additional security methods such as MFA, contextual authorization and user behavior (UEBA) to prevent an account from being taken over by a nefarious user.
How is it achieved in Identity Cloud?
In addition to MFA and contextual authorization, Identity Cloud offers an Autonomous Access service that can process an immense amount of contextual data to provide a high level of assurance on whether the person attempting to log into an account is the actual account holder.
Unlike traditional IAM solutions, Autonomous Access continuously inspects, learns, and adapts authentication decisions. By using heuristics to protect against known threats, combined with AI and machine learning, it can differentiate between normal behaviors and emerging threat patterns.
The following screenshot shows a user’s risky authentication attempts history in the activity detail of the Autonomous Access dashboard.
If the risk is too high the login journey can prompt for further identity verification methods to greatly limit the ability for a malicious actor to take over an account with just a stolen username and password
For further information on achieving ATO prevention with Identity Cloud, see:
- IAM 101 Series: What is Account Takeover?
- How Your Organisation Can Prevent Account Takeover (webinar)
- ForgeRock Autonomous Access
- Autonomous Access
- Autonomous Access White Paper
- Use case: Configure risk-based authentication in ForgeRock Identity Cloud
- Use case: Configure which authentication methods are invoked based on a risk score in ForgeRock Identity Cloud
Business benefits
ATO is often the source of data breaches, theft, and other fraudulent activities that lead to lost revenue, damaged brand reputation, and significant mitigation costs. ATO prevention not only safeguards customer data but also protects an organization’s intellectual property and sensitive business information from unauthorized access.
By proactively preventing ATO incidents, organizations can maintain a positive brand image and avoid the negative publicity associated with data breaches




