Use case overview
The ability to manage risk scoring models for artificial intelligence (AI) and machine learning (ML) is supported in the Autonomous Access service in ForgeRock Identity Cloud.
For this simple use case, we’ll demonstrate how the Autonomous Access Signal and Autonomous Access Decision nodes can capture risk inputs and evaluate for low, medium, high or unknown risk, and prompt for different authentication methods based on the risk score.
A similar, related use case can be found here: Use case: Configure risk-based authentication in ForgeRock Identity Cloud
Steps to achieve this use case
You’ll need an Identity Cloud tenant with the Autonomous Access add-on service.
Create an authentication journey
-
Sign in to the Identity Cloud admin UI using your admin tenant URL, in the format
https://<tenant-name>/am/XUI/?realm=/#/. -
Go to Journeys > New Journey.
-
Enter a unique name for the journey, select which identities will authenticate using this journey, (optionally) enter a journey description, and click Save.
-
Create a journey similar to this:
In this example user journey, end users with a low risk score can authenticate without further multi-factor authentication; end users with a medium or unknown risk score are required to authenticate with push authentication; and end users with a high risk score are denied access.
Node descriptions:
-
Platform Username - Prompts the user to enter their username. See Platform Username node for further information.
-
Platform Password - Collects the user’s password. See Platform Password node for more information.
-
Data Store Descision - Verifies that the username and password values match those in the data store configured for the realm. See Data Store Decision node for further information.
-
Autonomous Access Signal - Allows you to specify the heuristics and/or anomaly detection to be included in risk score generation during the AI/ML pipelines. See Signal node for further information.
-
Anonymous Access Decision - Takes the data sent by the Signal node and lets you direct the flow to actionable paths depending on where the risk score falls within the range of high, medium, low, and unknown scores. See Decision node for further information.
-
Send to: Push MFA - This is an Inner Tree Evaluator node that sends the user to a push MFA journey.
-
Autonomous Access Result - Provides the final outcome and risk prediction results from the AI/ML analytics. See Result node for further information.
-
-
Click the Autonomous Access Signal node and set the heuristics and/or anomaly detection to be included in risk score generation. By default, all options are selected.
-
Click the Anonymous Access Decision node and, if necessary, adjust the risk score definition for risk high, medium, low, and unknown scores.
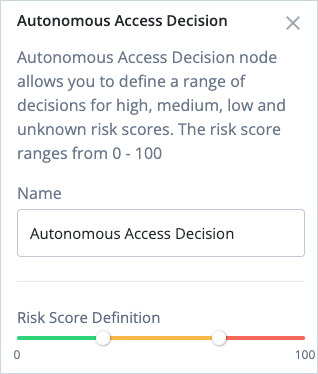
-
Click the Autonomous Access Result node linked to the failure outcome and select
FAILUREas the Final Journey Outcome.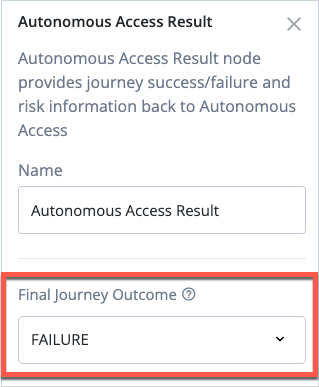
-
Click Save to save the Journey.
Conclusion
This simple use case has demonstrated how to easily implement a journey that determines the authentication method based on a risk score in Autonomous Access.
For further information on how Autonomous Access can help with AI-driven threat prevention, see ForgeRock Autonomous Access and the additional resources below.
Additional resources
Documentation:
- Autonomous Access
- Use case: Configure risk-based authentication in ForgeRock Identity Cloud
- Use case: Configure protection against credential stuffing and brute force attacks in ForgeRock Identity Cloud
- Use case: Manage risk scoring models (AI and ML) in ForgeRock Identity Cloud
Other assets:



