Overview
ForgeRock provides many resources on how to set up a social journey with various social providers. In most cases, following ForgeRock documentation and knowledge base articles is enough to set up a basic working environment. But sometimes things go wrong.
In this blog, we look into the flow of a successful social registration and authentication journey and show where it can break. We then address some of the most basic issues, leaving the more complex problems for another blog.
We assume that you have set up a journey for social registration and/or authentication following ForgeRock’s documentation or knowledge base articles (see links at the end of the blog).
The journey we are using in this blog contains both registration and authentication. It uses Google as Social Provider. The journey is shown below:
Overview of a successful flow
When everything goes according to plan, a social journey with Google contains the following steps:
- The end user accesses Identity Cloud which starts the social journey and displays the Google icon in the login page.
- The end user selects the Google icon and is redirected to Google for authentication.
- The end user authenticates to Google.
- The end user is sent back from Google with an ID token.
- The end user is logged in locally and sees their dashboard in Identity Cloud.
Where can it go wrong?
- The login page does not display the Google icon. See Issue 1.
- The end user selects the Google icon, is redirected to Google for authentication, but an error is displayed by Google. See Issue 2.
- The end user selects the Google icon, is redirected to Google, authenticates to Google, is redirected back to your tenant, but the tenant displays a login failure. See Issue 3.
Issue 1: What can you do if the login page does not display the Google icon?
-
Check that the correct journey is being called:
- Is it set as default? For reference, see Journeys - Overview - Default end-user journey.
- If it should not be set as default, edit the journey and select the Preview URL, then test again.
-
Verify that the Social Service provider is set up and enabled:
- Go to Native Consoles > Access Management > Services > Social Identity Provider Service.
- On the Configuration tab, ensure the toggle is set to Enabled.
- Select the Secondary Configurations and ensure that there is a “Client Configuration for Google”.
- Edit “Client Configuration for Google” and ensure the toggle at the top is enabled.
-
In your social journey, select the Select Identity Provider Node. Verify the configuration of the Filter Enabled Providers field:
- If it is empty, the login page displays all the social providers configured and enabled in step 2.
- If it is not empty, the login page only displays the social providers configured and enabled in step 2 for which the name corresponds exactly to one of the strings added in the field. So if your social provider is called “My Social Provider”, add the string “My Social Provider” in the field.
Issue 2: What can you do if the end user selects the Google icon, is redirected to Google for authentication, but an error is displayed?
-
Ensure the error is happening at the social provider: what is the URL displayed on the top of the error page? For Google, it will look like:
https://accounts.google.com/signin/oauth/error/v2?authError=<error_string>&client_id=<client_name> -
Find out if the social provider displays information about the error; for example, Google provides information such as:
-
If you select the error details link, it displays details such as:
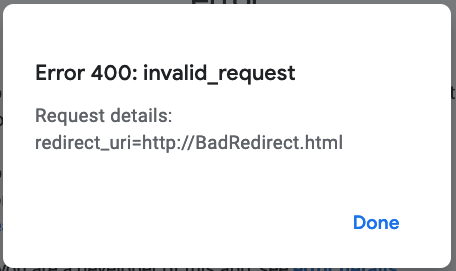
Common errors when Google is the Social Provider:
-
Error 400: redirect_uri_mismatch: the redirect URL should be
https://<your tenant>/loginin your social provider configuration in Identity Cloud. The same Redirect URL must be added when you create the application in the Google developer console. - Error 401: invalid_client: check that the ClientID value in the Google configuration in Identity Cloud corresponds to the ClientID in the Google developer console for your project.
- Error 400: invalid_scope: ensure the delimiter in the social provider configuration in Identity Cloud is a space (type a space in the field).
Issue 3: What can you do if the end user successfully authenticates to Google, is redirected to your tenant, but Identity Cloud displays a login failure?
The next step in this case is to find out if the social provider returns an ID token or not. See this post on how to find out if the social provider returns an id token: Did the social provider return an ID token?
We address troubleshooting in this case in the other videos in the series.
However, the error can happen before an ID token is returned. That is the case when the client secret for the social provider service in Identity Cloud is incorrect. That means that Identity Cloud can not identify itself as a trusted registered application with Google and no ID Token can be returned.
In such cases, there is little information stating what the issue actually is. It does not show in a HTTP trace, as it happens when the client tries to exchange the authorization code for an access token, which is not happening via the browser. You can find a trace of the issue in the Identity Cloud access logs where a 401 unauthorized is returned. In general though, if you have received an authorization code, but no ID token, double-check your service provider configuration, specifically the value of the client secret.
Conclusion
In this blog we described the stages of a successful social journey flow and described the most common issues that can happen before the social provider returns an ID token. In a following post we address the troubleshooting approach when an ID token is returned by the social provider, but the flow fails afterwards.
Other blogs or videos in this series:
- Step by step approach (blog)
- Did the social provider return an ID token? (video)
- Processing the ID token returned from a social provider (video)
- Checking the journey and node configuration (video)
- Finding the node that failed (video)
- Social registration troubleshooting walkthrough (video)


