Use case overview
Risk-based authentication is easily achieved using the Autonomous Access service in ForgeRock Identity Cloud.
Using the power of artificial intelligence (AI) to monitor login requests in real time, Autonomous Access can block malicious attempts and add authentication steps when it detects anomalous behaviors. This allows you to provide low-risk users with fast, easy access, while anomalous or suspicious attempts can trigger stepped-up authentication.
In this use case, we’ll demonstrate how to build a simple journey with risk-based authentication (RBA) rules to determine what outcomes to take for certain risk score ranges. The use case shows how the journey uses signals (such as anomaly detection, suspicious IP and impossible traveler) to make authentication decisions.
In our user example journey, end users with a low risk score can authenticate without further multi-factor authentication; end users with a medium risk score are required to authenticate with a one-time passcode; and end users with a high risk score are denied access.
Steps to achieve this use case
You’ll need an Identity Cloud tenant with the Autonomous Access add-on service.
Create a risk-based authentication journey
To create a simple risk-based authentication journey:
-
Sign in to the Identity Cloud admin UI using your admin tenant URL, in the format
<tenant-name>/am/XUI/?realm=/#/. -
Go to Journeys > New Journey.
-
Enter a unique name for the journey, select which identities will authenticate using this journey, (optionally) enter a journey description, and click Save.
-
Create a journey similar to this:
Node descriptions:
-
Platform Username - Prompts the user to enter their username. See Platform Username node for further information.
-
Platform Password - Collects the user’s password. See Platform Password node for more information.
-
Autonomous Access Signal - Allows you to specify the heuristics and/or anomaly detection to be included in risk score generation during the AI/ML pipelines. See Signal node for further information.
-
Autonomous Access Decision - Takes the data sent by the Signal node and lets you direct the flow to actionable paths depending on where the risk score falls within the range of high, medium, low, and unknown scores. See Decision node for more information.
-
OATH Token Verifier - Requests and verifies a one-time password (OTP) generated by a device such as a mobile phone. See OATH Token Verifier node for further information.
-
Autonomous Access Result - Provides the final outcome and risk prediction results from the AI/ML analytics. See Result node for further information.
-
-
Click the Autonomous Access Signal node and set the heuristics and/or anomaly detection to be included in risk score generation. By default, all options are selected.
-
Click the Anonymous Access Decision node and, if necessary, adjust the risk score definition for risk high, medium, low, and unknown scores.
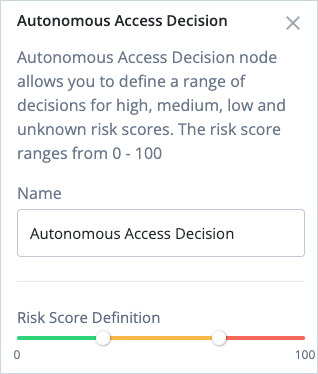
-
Click the Autonomous Access Result node linked to the failure outcome and select
FAILUREas the Final Journey Outcome.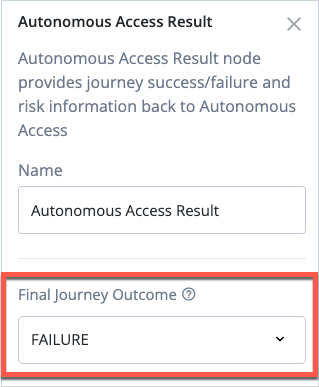
-
Click Save to save the Journey.
Configure the risk weighting
Autonomous Access includes a weighting configuration script that allows for customized calculation logic. This is intended for ForgeRock Professional Services to make the appropriate risk configuration modifications using business logic derived by your risk and security teams.
For further details, see Configuration in the Autonomous Access product documentation
IMPORTANT: Customers should not edit the script unless they know what they are doing. Misconfiguration of the file can result in an inoperable service. ForgeRock Professional Services group will make the appropriate risk configuration modifications.
Conclusion
This simple use case has demonstrated how to easily implement a journey for risk-based authentication using Autonomous Access. For further information on how Autonomous Access can help with AI-driven threat prevention, see ForgeRock Autonomous Access and the additional resources below.
Additional resources
Documentation:
Other assets:



